We know that cybersecurity incidents result in financial, reputational, and legal damage, and as a result, cybersecurity has found a place on the agenda of management teams and boards. Yet, those risks are constantly expanding.
The expansion of risks: Third-party vendors
Third-party vendors that provide in many cases specialized products and services to your organization have also increased in number over time. Multiple third-party vendors exist today, which can include call centres, ecommerce providers, collection agencies, outsourced information technology (IT) or software solution providers, paper shredders, amongst many others. These vendors may have suppliers, who in turn also have suppliers — so third-party vendors result in expanded “nth parties”.
These vendors typically have access to the organization’s information or network in some manner, which could provide access to your IT systems, operational technology (OT) systems, software and applications, or even your most sensitive data. Multiple third parties can be connected to your systems, and are collecting, aggregating or storing this data. They expand your organization’s supply or value chain, but also your risk profile.
Many of the risks that organizations face today can emerge from these third-party or nth-party vendors. The expansion of access points through vendors increases weak links in the value chain — something attackers are constantly scanning and looking for. Whether it is through your network, or an extended vendor’s link back to you, they can find an entry point and cause damage.
In the age of digital disruption, third-party vendors tend to be smaller in size, and more nimble. Yet, they may not have the same level of preparedness and guards in place and can be easy targets. Having a robust third-party risk management program is vital to mitigate these risks and improve outcomes for your organization.
The breach of information that took place at Target in 2013 was one of the first cases in the media to highlight the risks that third-party vendors can bring.
A vendor had access to the Target network, but because Target did not adequately secure access, threat actors found a way to enter the environment and access payment card information. The loss for Target from that incident is reported to be close to US$300 million.
Some newer incidents have also been reported in the media, including for some well-known technology firms through their vendors. There has also been an incident with attackers accessing finance and payroll directories of a large and well-known organization by finding a weak link in the supply chain, and then uploading the folders to the cloud.
If technologically advanced organizations have weak links through their vendors that attackers can exploit, they definitely exist in other organizations.
How well you are prepared, and how difficult and expensive you make it for the attackers, will determine how much you deter or reduce the impact of such attacks.
Managing your risks: Building third-party risk management programs
The point of discussing some of these risks and real-life examples is to establish that all risk cannot be eliminated. Across all organizations, it’s no longer a question of if but rather when an organization is breached through a weak link internally or in their value chain. However, the point is to minimize risks through robust third-party risk management (TPRM) programs, without the programs becoming too cumbersome.
The main objective of a TPRM program is similar to the current COVID-19 vaccine. It may not eliminate all risk of disease, but it significantly reduces the risk of extreme disease and outcomes.
In the case of TPRM, a robust program won’t entirely eliminate the likelihood of a breach, but it reduces the extreme outcomes an organization can suffer.
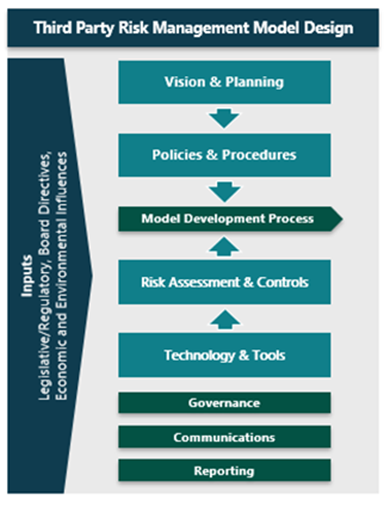
Third Party Risk Management Framework
Whether you are establishing a TPRM program due to regulatory requirements, to reduce your risks, or both, a basic step-by-step approach is outlined below:
- Develop the assessment framework you will use. This could include:
- Regulatory requirements such as those from the Office of the Superintendent of Financial Institutions, Payment Card Industry amongst others
- Standards or policies you are trying to align with such as ISO 27001/2
- External assessment criteria such as contract requirements or reputational impact
- The crown jewels in your organization it is most important to protect
- Conduct workshops with business stakeholders to review the assessment framework and identify your third-party service providers
- Develop standard reporting on threats and potential exposures leveraging standard templates to ensure consistency across vendor evaluations
- Identify and recommend cyber security assessment toolsacross the organization
- Review your program with the right stakeholders to ensure there is alignment in what the exact threats are and how solutions implemented mitigate the risk of those threats
- Perform third-party risk assessments based on risk levels of vendors with high risk vendors requiring more depth and frequent assessments
- Collect information from vendors
- Notify and engage your vendors in determining potential threats software/solutions following the organization’s steps taken to mitigate the risk. Open communication and understanding can lead to greater cooperation and ensure client service delivery is maintained
- Execute an assessment plan of your third-party provider through questionnaires or passive risk tools
- Gather information from vendors using an adaptive and agile approach, through self-assessments, clarification questions, evidence gathering, and if needed, additional testing
- Analyze the results you obtain from vendors, identify gaps, rate your vendors, and try to build in improvements, if needed
With the fast-evolving cybersecurity and third-party risks your organization faces, it’s important to think of your TPRM program as a marathon, and not a sprint. It’s better to get started right away, but continually adjust and plan for the long term, rather than treat it as an intensive one-time exercise.
If you’re looking to learn more about how you can decrease your risk with third-party vendors, contact Eugene Ng, CISSP, Partner, Cyber Security Leader, Eastern Canada, at [email protected] or 905-247-3280






